Disk encryption (Aalto-Linux)
Deployment
Deploying of disk encryption requires performing a complete re-install on the computer.
If you make a re-install on a computer that is already in use, remember to transfer the files on the computer to a safe location because the entire disk will be erased during the installation.
1. If you want to install a computer, please contact the administrator or the IT service desk.
2. The computer will require the setting of a password after the installation and when the computer is powered up for the first time. Think of a good password because your selection will be a permanent one, in practice.

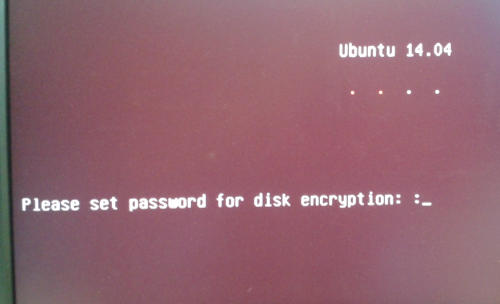
3. Enter the password twice and memorize it. Beware of using any uncommon special characters in your password. Ubuntu contains a long-standing and well-known bug that can change the keyboard layout between the time when the password is set and when it is prompted.
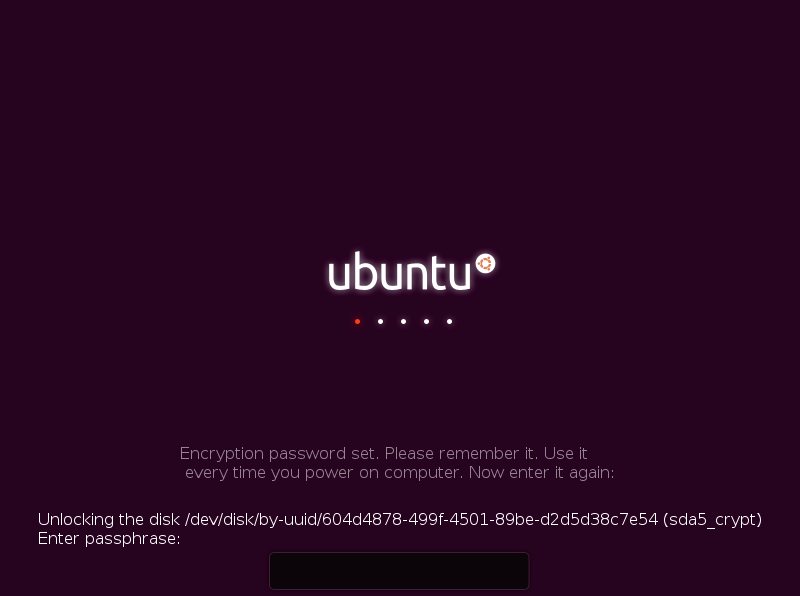

4. Once the password has been set successfully, it must be entered one more time to open the disk.
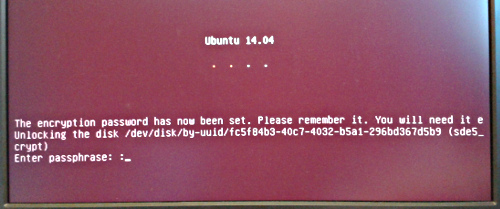
5. From here on, the computer will start in the usual manner.
Use
Every time the computer is powered up, it will prompt for a disk encryption password before the start-up process continues.
Processing of keys (special cases)
Under normal circumstances, there is no need to touch the disk encryption passwords (keys).
You may need the instructions below in the following cases, for example:
- your project requires that there may not be a centralized (computer-specific) backup key
- it is necessary to add more keys for a laptop in shared use, for instance.
There can be a maximum of seven keys. Processing the keys requires root privileges.
Viewing the LUKS header
For example, with the command
| cryptsetup luksDump /dev/sda5 |
it is displayed like this
|
LUKS header information for /dev/sda5 Version: 1 Cipher name: aes Cipher mode: xts-plain64 Hash spec: sha1 Payload offset: 4096 MK bits: 512 MK digest: 2d 20 db f4 d6 17 c3 5f eb f9 c9 eb 10 47 9d 1d 55 7e d8 4a MK salt: 7e 0b 22 20 38 fa 76 0e 65 36 93 b7 9e cf b4 c0 ed 38 f7 e4 77 97 06 75 43 ce 87 a4 a9 a1 7d 72 MK iterations: 46500 UUID: 21bf98d4-27e3-409d-ad12-1c0b156b992e Key Slot 0: ENABLED Iterations: 189069 Salt: cc 6f 1b 78 b4 53 7f a6 6a 0b cb cb 93 17 1f 87 0d 84 31 58 b8 35 b1 9d e1 b2 d6 84 91 d2 ee c0 Key material offset: 8 AF stripes: 4000 Key Slot 1: ENABLED Iterations: 237476 Salt: 41 68 0d 7d d4 e4 6f e6 f5 2a 3e 9d 30 75 96 27 69 0c 12 c8 f1 fc d3 11 5b 61 eb c9 c6 7a 9a 02 Key material offset: 512 AF stripes: 4000 Key Slot 2: DISABLED Key Slot 3: DISABLED Key Slot 4: DISABLED Key Slot 5: DISABLED Key Slot 6: DISABLED Key Slot 7: DISABLED |
Deleting a key
Below,<n> is slot number... the centralized spare key is in slot 1.
Below, <device> in Aalto-Linux is usually /dev/sda5, but it can be something else in exceptional cases.
| cryptsetup luksKillSlot <device> <n> |
Adding a key
| cryptsetup luksAddKey <device> |
Changing a key
| cryptsetup luksChangeKey <device> |
releted instructions
IT Services
- Published:
- Updated: